Pocket Pass Enrollment
Note
PhenixID Pocket Pass Enrollment allow users to activate themselves for strong authentication with one-time password (OTP), using PhenixID Pocket Pass application. The activation portal reduces user interaction to an absolute minimum.
In this guide you will configure:
- Configure a connection to the LDAP store where the users are located
- Enable Pocket Pass activation portal
Warning
Pocket Pass is deprecated - we don't encourage the use of Pocket Pass, and we only offer limited support for it, the functionality has been replaced by One Touch.
Start guide
Start the guide by clicking the '+' sign next to Pocket Pass Enrollment
Guide steps
You navigate the guide using the previous and next buttons at the bottom of the page. You can also choose to cancel the guide at any time (information entered will be lost).

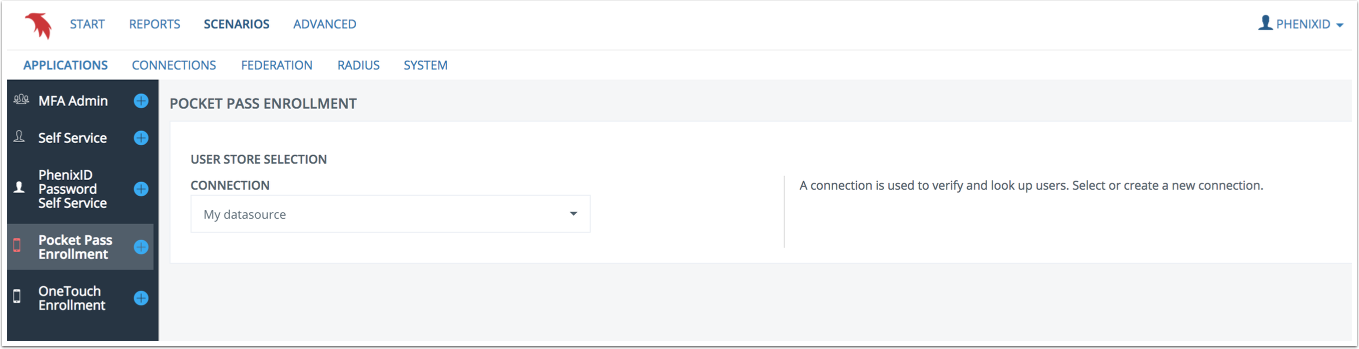
User store selection
Select an existing connection to an LDAP user store or create a new connection.
To create a new connection, follow the steps in the this guide.
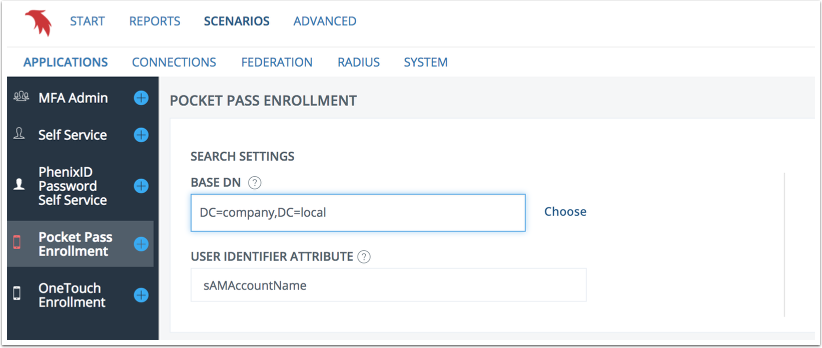
Search settings
Manually enter the search base to use or select it by using Choose . Search base is the starting point in the directory tree structure from where searches are made. Search is done with scope "SUB". This value is mandatory with LDAP DN as required syntax.
Also enter the attribute identifying your users (like uid, mail or samaccountname).
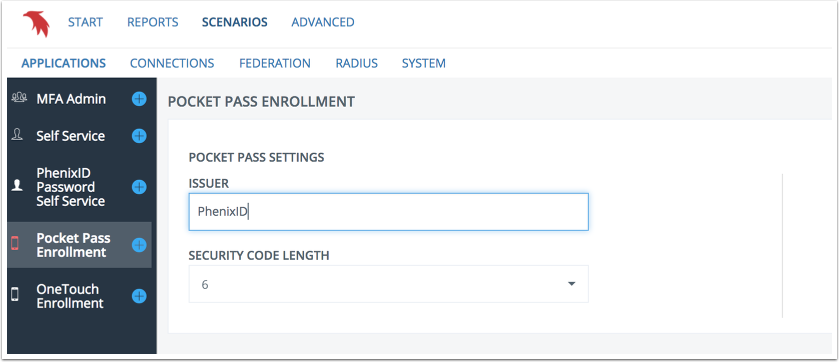
Pocket Pass settings
Configure Issuer and code length.
- Issuer is a logical name, such as organization or unit, used for naming profiles in Pocket Pass application. The issuer name will be seen in the lower left corner, in combination with username.
- Security code length is the number of digits used for OTP in the Pocket Pass profile.
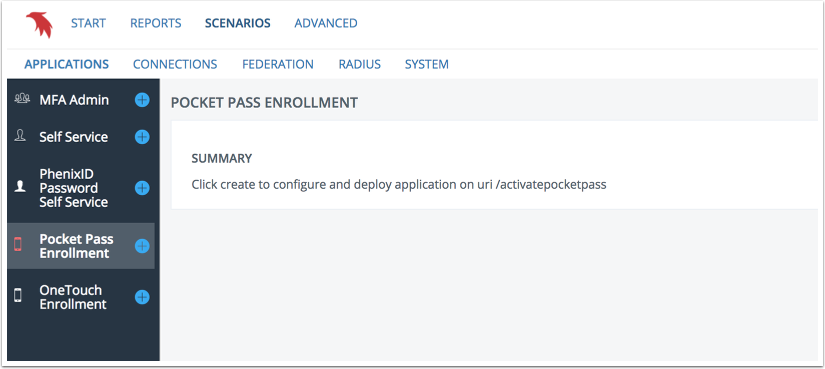
Summary
Click Create to complete the scenario.
The activation portal can now be found at the URI displayed below.
Example: https://dnsnameofPhenixIDServer:8443/activatepocketpass
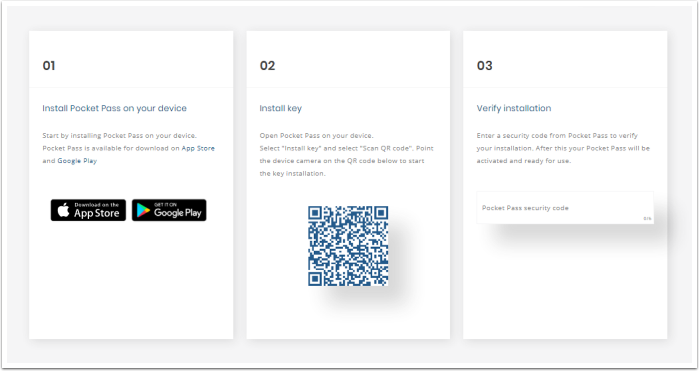
Activation portal
Log in to the portal with username and password against the user store.
Multifactor authentication can be added to the login scenario.
When logged in, enrollment can be made for Pocket Pass profile(s).
Edit guide configuration
You can edit and delete your pocket pass enrollment configuration by selecting it in the lefthand menu.
When you click save, the configuration will be updated and the server will instantly restart affected components to apply your changes.
Delete removes all configuration created by the guide but not shared components (i.e components that could be used by other configurations like connections).

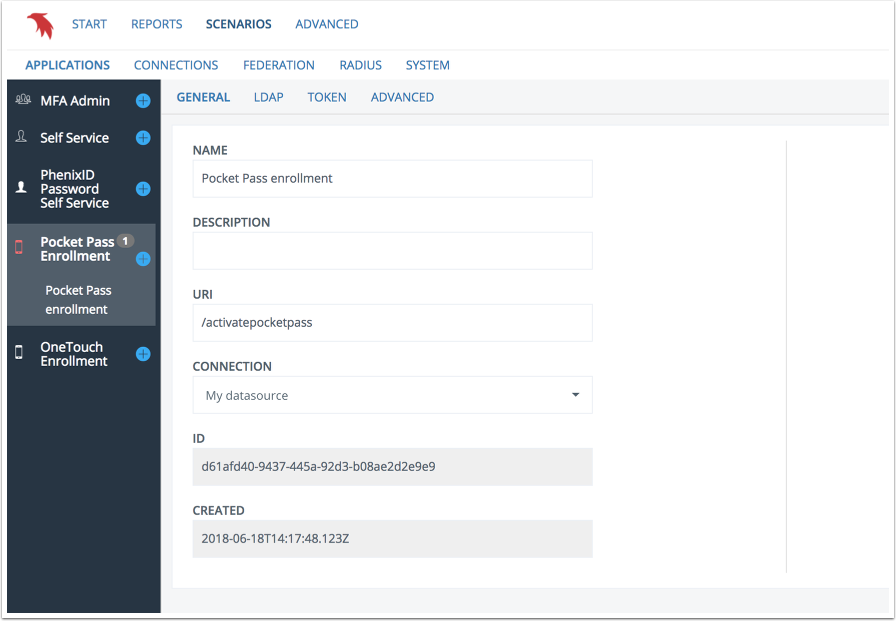
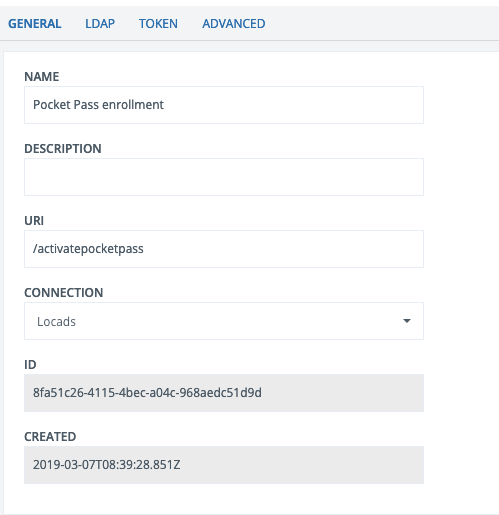
General
General application settings.
- Name: Logical name of application (displayed in left side menu).
- Description: Application description
- Connection: User store connection. To add a new connection, use the LDAP connection guide and then choose the new connection.
- URI: The http context (path) to the application. Must be unique in the current configuration (i.e not in use by another application) and start with a '/'
- ID: Internal configuration ID
- Created: Timestamp when configuration was created
LDAP
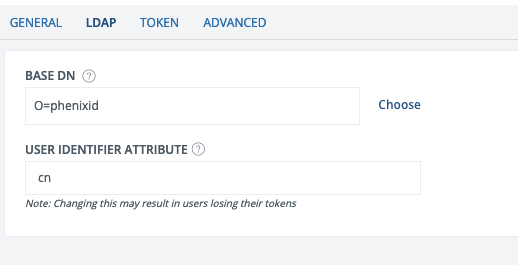
LDAP Settings
- Base DN: DN to use as base for user search. Add manually or use Choose to browse your directory.
- User identifier attribute: Attribute identifying users. Used for bind during login and visible in application.
Token
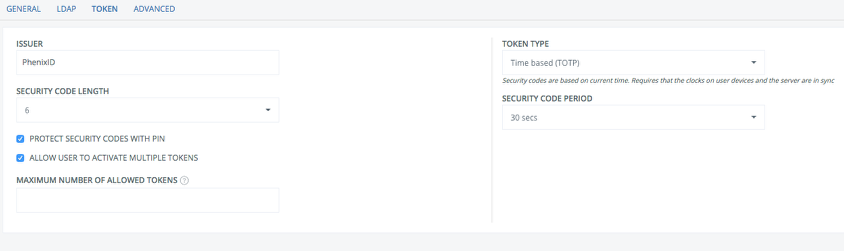
Token Settings
- Issuer: Name of organization or unit issuing the token. Identifies the the token (key) in the Pocket Pass client in combination with username.
- Security code length: Length of OTP security codes (6 or 8 digits).
- Protect security codes with PIN: If access to the token should be protected by a PIN code.
- Allow user to activate multiple tokens: If multiple tokens are allowed.
- Maximum number of allowed tokens: Limit the number of tokens a user can enroll. Leave blank for unlimited number.
- Token type: Time based or counter based.
- Security code period: For how long each OTP is valid, 30 or 60 seconds.
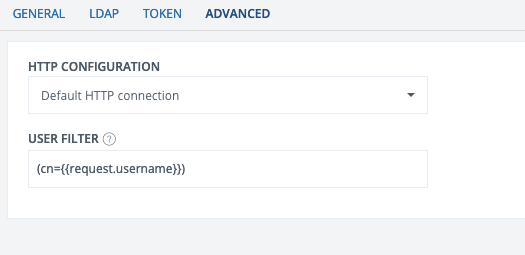
Advanced
Advanced Settings
- HTTP configuration: The HTTP configuration to use. If needed, new configurations can be added under the Connections menu.
- User filter: User search filtering