Activate One Touch - Change authentication method
Warning
Please note, this document is using the legacy authenticators - in order to use the new protocol agnostic authenticators, you need to apply relevant modifications to the configuration examples outlined in this article.
This document describes how to change authentication method (by default it's protected with username/password) for the Activate One Touch application. This is done using an internal SAML federation flow where Activate One Touch will act as a SAML SP connected to a SAML IdP.
Requirements
- PhenixID One Touch activation application configured
Configure authentication method
- Login to Configuration Manager
- Set up a SAML IdP with the required authentication method using Scenarios->Federation-><Method>.
- Set the entityID to ACTIVATEONETOUCH-IDP
- Set NameID to the attribute containing the userID (such as userPrincipalName, sAMAccountName or mail)
Protect the One Touch activation application with a SAML SP
Get keystore id
- Login to Configuration Manager
- Navigate to Advanced -> Keystores
- Locate the the keystore object with "name":"Default auto generated server keystore"
- Copy the id value from the keystore
Add SAML SP base configuration
- Navigate to Advanced -> SAML 2 Service Providers
- Add this object
{
"id": "ACTIVATEONETOUCH-SP",
"keystoreSign": "<REPLACE_THIS_WITH_THE_KEYSTORE_ID_COPIED_IN_PREVIOUS_STEP>",
"entityID": "ACTIVATEONETOUCH-SP"
}
Example:
{
"id": "ACTIVATEONETOUCH-SP",
"keystoreSign": "f2b90db8-b188-449b-8edc-163b8e3091cf",
"entityID": "ACTIVATEONETOUCH-SP"
}
Add SAML SP authenticator
- Navigate to Advanced -> Authentication - HTTP
- Add this object
{
"id": "activateonetouchsp",
"alias": "activateonetouchsp",
"name": "SAMLServiceProviderAuthN",
"description": "SAML service provider for activate one touch",
"configuration": {
"successURL": "/activateonetouch/",
"sp": "ACTIVATEONETOUCH-SP",
"pipeID": "pipeAssertionConsumerAO",
"acsUrl": "/activateonetouch/authenticate/activateonetouchsp",
"entityID": "ACTIVATEONETOUCH-SP",
"targetIDP": "ACTIVATEONETOUCH-IDP"
}
}
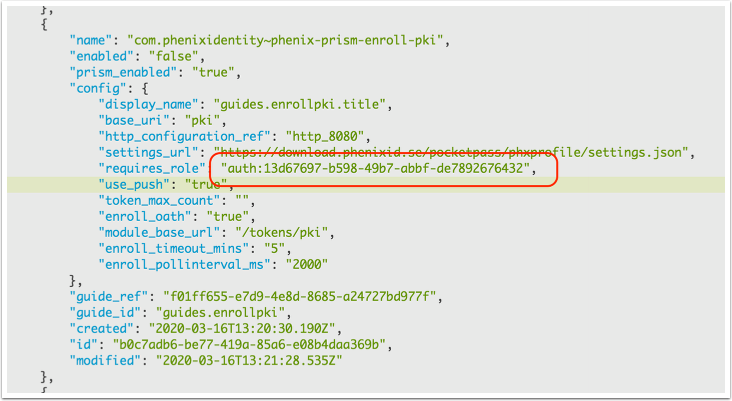
Get the required role value
- Navigate to Advanced -> Modules
- Locate the module object with "name": "com.phenixidentity~phenix-prism-enroll-pki"
- Copy the requires_role value
Add pipe
- Navigate to Advanced -> Pipes
- Add this pipe:
{
"id": "pipeAssertionConsumerAO",
"valves": [
{
"name": "AssertionConsumer",
"config": {}
},
{
"name": "FlowFailValve",
"config": {
"message": "User does not exist",
"exec_if_expr": "flow.items().isEmpty()"
}
},
{
"name": "PropertyAddValve",
"config": {
"name": "roles",
"value": "<REPLACE_WITH_PREVIOUSLY_FETCHED_REQUIRED_ROLE_VALUE>",
"enable_multi_value": "true"
}
}
]
}
Example pipe:
{
"id": "pipeAssertionConsumerAO",
"valves": [
{
"name": "AssertionConsumer",
"config": {}
},
{
"name": "FlowFailValve",
"config": {
"message": "User does not exist",
"exec_if_expr": "flow.items().isEmpty()"
}
},
{
"name": "PropertyAddValve",
"config": {
"name": "roles",
"value": "auth:13d67697-b598-49b7-abbf-de7892676432",
"enable_multi_value": "true"
}
}
]
}
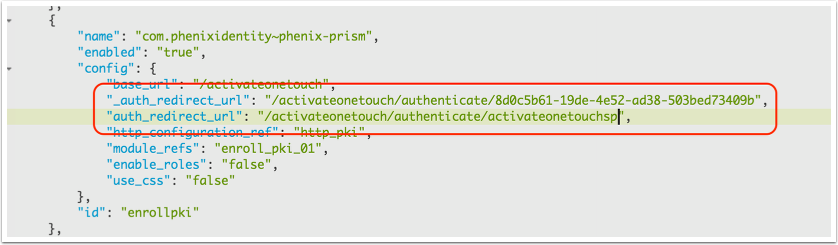
Enable the SAML SP authenticator
- Navigate to Advanced -> Modules
- Locate the module with "base_url": "/activateonetouch"
- Comment out the current auth_redirect_url parameter by adding another _ prefix
• Add the parameter "auth_redirect_url": "/activateonetouch/authenticate/activateonetouchsp"
See example:
Test
- Browse to
https://<phenixid_server_domain>:<port>/activateonetouch/ - The browser should be redirected to the IDP authenticator
- Authenticate
- The browser should be redirected to the SP
- You should now be logged in to the Activate One Touch application
Error tracing
Check the logs for errors.