Trigger ADFS sign-out when using PhenixID Authentication Services as relying party (SAML SP)
Warning
Please note, this document is using the legacy authenticators - in order to use the new protocol agnostic authenticators, you need to apply relevant modifications to the configuration examples outlined in this article.
Summary
This document will guide you through the steps to sign out the user from ADFS when using PhenixID Authentication Services as a SAML SP (relying party) against ADFS as SAML IdP.
Background
PhenixID Authentication Services can be used as a SAML SP against ADFS to trigger ADFS authentication for the user. This is useful in these use cases:
- Protect a PhenixID web application with ADFS login (using the SAMLServiceProviderAuthN authenticator).
- Protect an OpenID Connect RP with PhenixID Authentication Services, consuming the authentication from ADFS (using the OIDCToSAMLBroker authenticator)
- Protect a SAML SP with PhenixID Authentication Services, consuming the authentication from ADFS (using the SAMLSPBroker authenticator)
System Requirements
- PhenixID Authentication Services 3.2 or higher
- PhenixID Authentication Services setup as a SAML SP (see use cases above).
- PhenixID Authentication Services SAML SP setup as a relying party in ADFS.
Instruction
ADFS
- Open the AD FS management app on the ADFS server
- Relying partys -> Locate the PhenixID Authentication Services trust
- Doubleclick to open RP properties
- Click Endpoints
- Click Add SAML
- Select SAML Logout
- Add trusted url =
https://<adfs_server_domain>/adfs/ls/?wa=wsignout1.0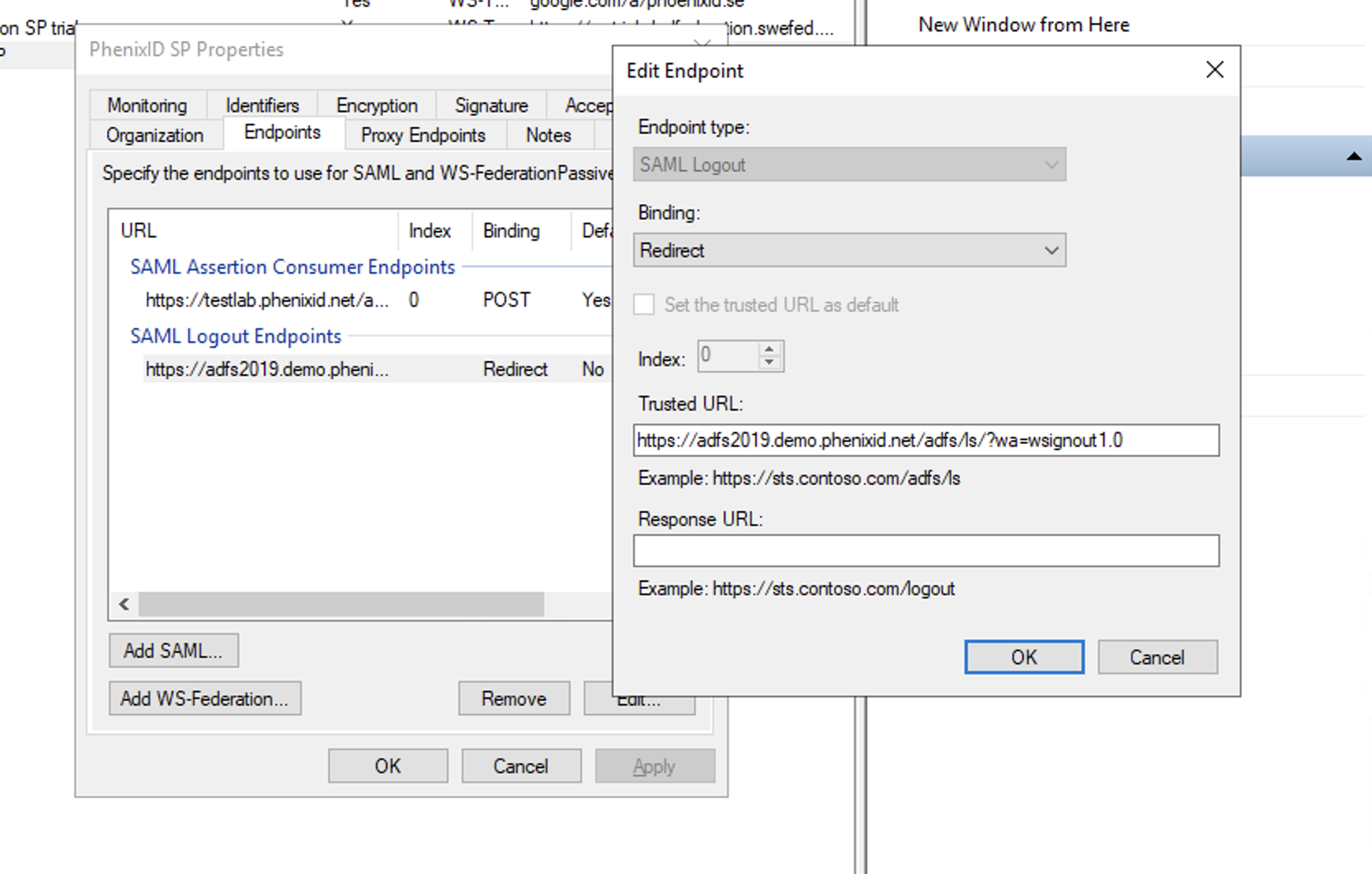
- Click OK
- Click OK
PhenixID Authentication Services
- Fetch the ADFS logout URL (On pattern
https://<adfs\_server\_domain>/adfs/ls/?wa=wsignout1.0, see above for details.) - Whitelist the logout URL as an allowedLogoutTarget using this instruction.
- URL-encode the logout URL (using an online tool). Copy the result. Example result:
https%3A%2F%2Fadfs.2019.demo.phenixid.net%2Fadfs%2Fls%2F%3Fwa%3Dwsignout1.0 - Login to configuration manager. Based on your use case, perform the following changes:
- Protecting a PhenixID web application with ADFS login (using the SAMLServiceProviderAuthn authenticator).
Advanced->Modules
Find the module/application
Change/add the parameter
logoff_uriwith the nextTarget parameter pointing to the logout URL (above).Example:
"logoff_uri": "/activatefido/authenticate/logout/?nextTarget=https%3A%2F%2Fadfs2019.demo.phenixid.net%2Fadfs%2Fls%2F%3Fwa%3Dwsignout1.0"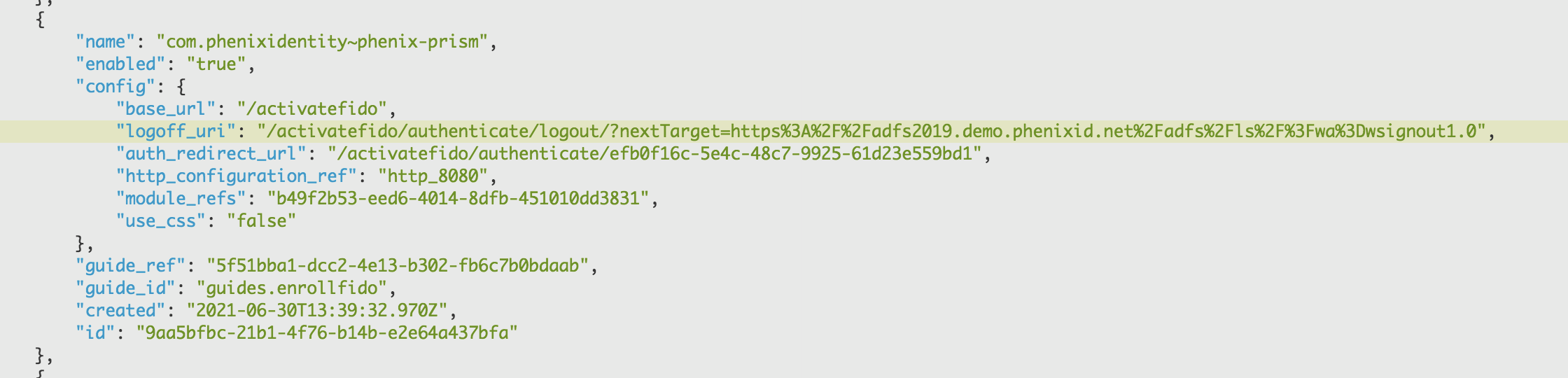
Change the first uri value (in above example /activatefido) to suite your application/module.
Click Stage changes and Commit changes
- Protect an OpenID Connect RP with PhenixID Authentication Services, consuming the authentication from ADFS (using the OIDCToSamlBroker authenticator)
Advanced->OIDC OP
Locate your OpenID Connect Provider
Change end_session_endpoint =
https://<pas_domain>/oidc/authenticate/logout/?nextTarget=https%3A%2F%2F<adfs_domain>t%2Fadfs%2Fls%2F%3Fwa%3Dwsignout1.0Example:
Click Stage changes and Commit changes
- Protect a SAML SP with PhenixID Authentication Services, consuming the authentication from ADFS (using the SAMLSPBroker authenticator)
Advanced->SAML Identity Providers
Locate your SAML IdP used
Change/add
postSLOURL = https://<pas_domain>/saml/authenticate/logout/?nextTarget=https%3A%2F%2F<adfs_domain>t%2Fadfs%2Fls%2F%3Fwa%3Dwsignout1.0Example:
Click Stage changes and Commit changes
- Protecting a PhenixID web application with ADFS login (using the SAMLServiceProviderAuthn authenticator).